Using sensitivity labels with SharePoint document libraries
What are sensitivity labels in Microsoft 365?
Sensitivity labels are used to classify content and protect content. They are the digital equivalent of ‘stamping’ a document to share how information can be used, shared or viewed.
Microsoft Purview (previously known as Microsoft 365 compliance) sensitivity labels can be applied to emails, documents and Microsoft 365 containers including Teams, SharePoint sites, and Microsoft 365 Groups.
In this article, we’ll focus on tips for applying sensitivity labels to documents saved in SharePoint document libraries.
Why use sensitivity labels for documents saved in SharePoint?
Data is constantly being created, edited, shared, and stored by employees and sometimes partners. Whatever someone’s role in an organization, they work with sensitive and confidential information, and properly classifying and protecting this data are critical.
When you enable a sensitivity label on a document in a SharePoint library it tags or stamps the content. Two things then happen:
The tag is embedded in the file and will follow it everywhere it goes.
Protective behaviors are enabled such as content watermarks, limits for who can view the document, or encryption. With Microsoft end point protection enabled you can even prevent an item from leaving your organizational control.
Aside: what about using security and permissions instead?
Sensitivity labels do more than securing content to appropriate audiences. You can configure sensitivity labels to encrypt content, prevent copying, restrict downloading or even prevent Print Screen capability. The unique behaviours possible with Microsoft Purview sensitivity labels are what make them useful in combination with Microsoft 365 security and permissions.
Examples of using sensitivity labels
Apply labels to files and emails
Automatically classifying and protecting files stored in SharePoint are the most common scenarios we see clients wanting to enable.
There are two different ways to apply a sensitivity label to SharePoint content:
Client-side labeling when users edit documents. This method can recommend a label to users, as well as automatically apply a label. The user can decide to accept or reject the label.
Service-side labeling when content is already saved in SharePoint or OneDrive. This method is setup through an auto-labeling policy (more on that below).
Here’s what prompting users to manually apply labels in Word looks like:
Client-side labeling through a recommendation in Microsoft Word
This goes to the Sensitivity toolbar option to select a label:
Select label from toolbar
Most of the time however, we want labels to be automated so that users don’t have extra steps in their workflow. We recommend setting a label automatically based on the content of the documents, as users will likely not use the manual setting.
Apply watermarks automatically
Another common scenario is using sensitivity labels to apply a watermark or header/footer to a document if it’s highly confidential. Below is an example of watermarks applied automatically to a document when it is labelled as Highly Confidential:
Example of document watermark, image courtesy of Microsoft
Restrict default sharing behaviour for links
If you have a mix of documents across SharePoint sites where some have a higher level of sensitivity, you can configure a sensitivity label to have different default link sharing setting. Most users don’t change defaults, so this is one way to reduce the risk of accidental over-sharing.
A more widely applicable scenario is for OneDrive. OneDrive is typically a mix of work-related and personal files. In this case, you can set sharing links to default to:
Documents labeled General have a default setting that restricts to people in your organization.
Documents labeled Personal or Public have a default setting that allows sharing to anyone with the link.
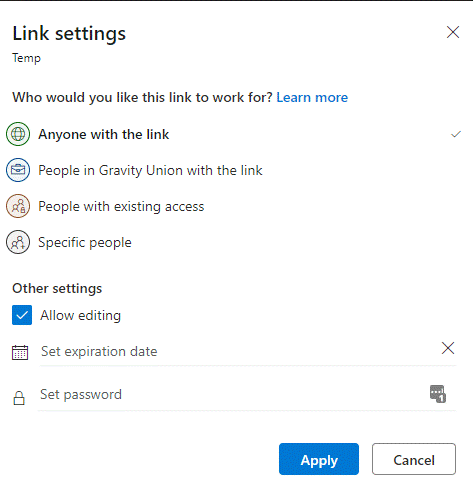
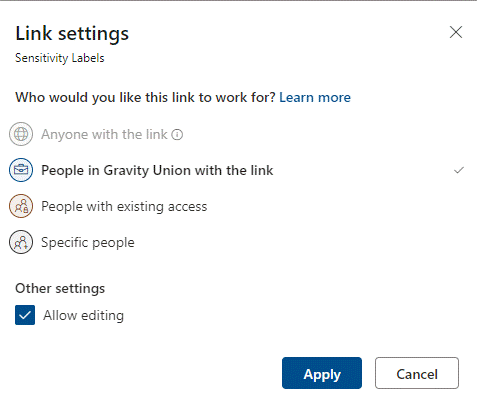
Configuring this option with sensitivity labels changes the experience for sharing links:
Link settings for Public documents vs. General documents
The configuration steps for changing link sharing defaults for sensitivity labels are beyond the scope of this article since it is done with PowerShell, but you can find instructions here.
A starting point for the label structure
Where to start with labels? We recommend rolling out a structure that is as simple as possible for users to understand, so that they know when to use labels, and what happens when they do.
A useful starting point is to start with only labeling Confidential documents. One common way to start is with one label available for a subset of users who deal with Confidential documents such as employee files, contracts, financial info and legal docs. Ideally, Confidential labels apply automatically based on document content and/or document location (more on that later).
As your organization gains more experience with sensitivity labels, the label categories can grow to include:
Non-Business / Personal: This is data that does not belong to the organization, and is not encrypted or tracked.
Examples: Vacation photos, personal email, information not related to workPublic: This is data that is approved for public consumption, and is not encrypted or tracked.
Examples: Job postings, blog articles, marketing videos, customer service response to a product question, annual reports or letters, maps, court casesGeneral: This is the organization data that is NOT intended for public consumption. This data is shared with internal employees and external partners as needed, and most likely is not encrypted and tracked.
Examples: Internal news, onboarding content, corporate policies, human resources info and guides, company-wide email, any non-sensitive business contentConfidential: This data is intended for specific audiences or employees only, and usually IS classified and protected with encryption. Generally, employees can edit, reply, forward, print and can unprotect content with appropriate justification. Note: if your organization works with partners, contractors or vendors, there could be two categories under Confidential: Confidential – Employees and Confidential – Employees Extended.
Examples: product specifications, marketing campaign for new product, email to staff about new security measures, financial reports, business operation data, employee performance reports.Highly Confidential / Top Secret (optional 5th category): If you follow strict compliance regulations such as in healthcare (HIPPA) or in government, we recommend the 5th category for “Highly Confidential.” Permitted employees can still edit, reply, forward, print and information should be protected with encryption.
Examples: Competitive intelligence, banking information, board of directors communication, upcoming quarterly projections, medical study data, security clearances, blueprints, HIPPA/GDPR/FDIC regulated data
How to set up your first label
At a high level, the steps to setup a sensitivity label are:
Decide on the Sensitive Information Type – use a Microsoft provided one, or create a custom type
Create the label and define what the label does (adds header/footer, watermark, encryption, etc.)
Publish the label with a label policy that targets users/groups/sites
Step 1: Decide on a Sensitive Information Type
The critical part of auto-labelling is to configure the pattern matching so that Microsoft 365 knows how to find sensitive documents in your SharePoint environment. Luckily, Microsoft Purview comes with several pre-configured sensitive information types (SITs) for common sensitive data such as credit card numbers, passport and ID numbers.
To label organization-specific documents such as as merger documents, confidential project information, financial reports or contracts, you need to create custom sensitive information types or trainable classifiers. Creating a custom SIT is beyond the scope of this article, but there is plenty of help in Microsoft documentation: Create custom sensitive information types - Microsoft Purview (compliance) | Microsoft Docs
If you’re testing out using sensitivity labels, you can move ahead with Steps 2-3 below without configuring any sensitive information types, and use the ones provided by default.
Step 2: Create and define the label
For Step 2, go to the Compliance Center > Information Protection > Create new label:
Create a new label in Microsoft Purview (previously Microsoft 365 Compliance)
From there, enter a name and description for the label and choose a scope. The settings for the purposes of this article that affect SharePoint documents are:
Sensitivity Label settings for files and emails
If you’re only doing classification with the label, you can leave these boxes unchecked. Most of the time though, you want to use behaviours, since they are the key benefits of labels.
The Admin interface will guide you through encryption and content marking settings including the watermark options:
Watermark options including colours, fonts and placement of text
The auto-labelling settings are the most important step of this flow:
Select the sensitive information type (SIT) or trainable classifier
Here is where you select the SIT or trainable classifiers that are included with Purview, or that you set up previously.
There are several pre-configured options for sensitive info types including credit card number formats, country specific IDs, etc. If you’re starting out with compliance settings, pick a pre-configured option. For example, for sensitive Canadian customer data that you want to mark with a label, add these settings:
Examples of default sensitive information types
After this, there are a few more settings to choose from for controlling external access for the group/site container. More detail on all the settings is provided in Microsoft documentation: Create and publish sensitivity labels - Microsoft Purview (compliance) | Microsoft Docs
Step 3: Publish the label
To publish the label, a label policy is needed. Label policies are different from retention policies, which are published to locations such as all Exchange mailboxes. Sensitivity labels are published to users or groups.
On the Label policies page, select Publish label to start creating a policy. Choose which label to publish, and if you’re publishing a sub-label, remember to publish the parent label as well.
Choose label(s) to publish
The next few steps provide options for the settings on the policy. These settings change depending on the label scope – for example, for a label that applies to Files & Emails only, you won’t see the options for applying labels to groups and SharePoint sites.
At minimum, you likely want to apply the label by default to documents if you’re working with SharePoint document libraries:
Apply default label to documents
Finishing all the label policy steps will publish the label. It will take 24 hours or less for the label changes to be available in Microsoft 365 services.
Notes and Limitations
Balance collaboration with compliance
Sensitivity labels are sometimes not deployed across an organization because they add another layer of complexity to the collaboration experience of employees.
Even with automatic labelling, end users will see new icons and messages through the Microsoft 365 platform. Some of these messages can look concerning or like issues. For example, clicking on the sensitivity label icon can show something like this:
Icons in a SharePoint document library
Sensitivity labels can also cause behaviour that end-users don’t expect. For example, restricting copying might seem like a good idea for Highly Confidential files, but this doesn’t only prevent using the copy (Cmd/Ctrl+C) function. It also blocks taking a Print Screen and screen sharing on Teams. This is a headache if you want to share a document on screen during a meeting!
Encryption can slow down the loading time for users, so use it sparingly and only for the most confidential of documents. Here’s what the admin warnings look like if you use encryption and auto-labeling:
Encryption warning
When designing labels, keep in mind that you want to balance the productivity of collaboration with compliance. We recommend deploying sensitivity labels to a smaller subset of users before making them available across an organization and using features such as Encryption sparingly. We provide consulting services to help you with that setup.
Change management
Another consideration is to roll out sensitivity labels with end user messaging and a change management strategy. New icons and information controls show up across documents, Teams and SharePoint sites. These can either be alarming, easily ignored, or frustrating if people don’t know why they are there! Explain the label definitions, and what happens when labels are enabled by using all your communication channels.
There is an option to link to a custom URL or page which describes your organization’s sensitivity label hierarchy, which we recommend you make use of.
Limitations for auto-labeling
Auto-labeling is a premium license feature, and there are some limitations to be aware of:
Maximum of 25,000 automatically labeled files in your tenant per day.
Maximum of 100 auto-labeling policies per tenant, each targeting up to 100 sites
A label won’t apply if the file is open or attached to a list item
Office files for Word (.docx), PowerPoint (.pptx), and Excel (.xlsx) are supported - with PDF support likely coming in the future, at the time of this writing.
More details about auto-labeling are here: Automatically apply a sensitivity label in Microsoft 365 - Microsoft Purview (compliance) | Microsoft Docs
Plan to apply sensitivity labels to new and existing documents
It used to be that when you published sensitivity labels, the labels only applied to newly created or uploaded documents in SharePoint document libraries. This means that all the existing documents in your system before setting up sensitivity labels don’t receive the classification or protection benefits.
This is changing with a couple of Microsoft 365 roadmap items, but note the feature for Office apps is in preview, at the time of this writing.
Summary
It’s worth investing time in planning how to use sensitivity labels to protect and classify your most critical content. Reach out if you need help or advice with sensitivity labels or creating sensitive information types.